
Ships Running Blind: How GPS Spoofing Is On The Rise
Authored by Chris Summers via The Epoch Times (emphasis ours),
There has been a big increase in the number of Global Positioning System (GPS) spoofing or jamming attacks, aimed at messing with the GNSS (Global Navigation Satellite System) data, which is standard on all international shipping.
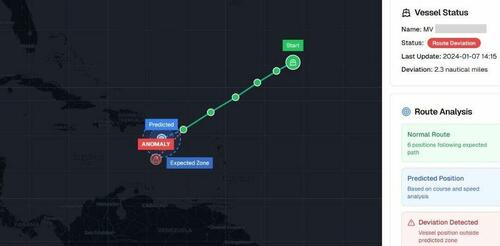 A screenshot from Israeli maritime cybersecurity firm Cydome’s system, of an example of a GPS spoofing incident involving a ship in an undisclosed location on Jan. 7, 2024. Courtesy of Cydome
A screenshot from Israeli maritime cybersecurity firm Cydome’s system, of an example of a GPS spoofing incident involving a ship in an undisclosed location on Jan. 7, 2024. Courtesy of CydomeJeroen Pijpker, from NHL Stenden University of Applied Sciences in the Netherlands, told The Epoch Times they had recorded 400 GPS spoofing and jamming incidents in their database—25 percent of which related to actual vessels—but he believed it was the “tip of the iceberg.”
Nir Ayalon, the founder and CEO of Cydome, a maritime cybersecurity firm based in Israel, told The Epoch Times that 95 percent of incidents caused by spoofing or jamming do not end up making the news.
He said Cydome had seen a 500 percent increase in GPS spoofing and jamming this year, with a 2,000 percent rise in the number of maritime blackspot areas.
GPS jamming was blamed for a collision in the Gulf of Oman in June 2025, between the Liberia-flagged tanker Front Eagle, and the Adalynn, which has been identified by Lloyd’s List—the bible of the shipping industry—as a “dark fleet” vessel.
Ayalon said that GPS spoofing is sometimes carried out by the operators of ships in order to disguise their location or identity, but it is also perpetrated as a hostile act.
He said that was believed to be the case with the MSC Antonia, which ran aground in May in the Red Sea, close to the southern end of the Suez Canal, en route to Malta from the Saudi Arabian port of Jeddah.
‘Manipulation of the Data’
“When we talk about GPS spoofing or jamming, we have several methods that organizations will use,” Ayalon said. “So there is the manipulation on the RF [radio frequency] data from the satellite to the vessel or to the antenna itself, but we have also manipulation of the data itself.”
He said spoofing or jamming could be carried out in two ways—by intercepting GNSS messages from the antenna to the transceiver, or by manipulating the AIS (Automatic Identification System) data, which all ships use.
An attacker will manipulate this data, which is easier because it’s on the web, Ayalon said. “It does not require any encryption or any authentication, so you can basically add any information that you want there.”
“It’s very easy to get into AIS data,” he said.
He said GPS spoofing could, in effect, render ships invisible—in other words, they would show up on the map in a certain location, but in reality, they would not be there.
Referring to the MSC Antonia incident, he said: “Basically, their location was manipulated and the ship autopilot tried to fix the path to the path that it thought was the right one … so the ship grounded.”
“If you would look at the place where the AIS is telling you that the ship is … there’s no ship there,” Ayalon said.
Sometimes, spoofing was carried out by bad actors who were trying to damage a specific vessel, he said.
There were also reports of Russian oligarchs using spoofing to hide the location of their megayachts in 2022, when sanctions against Russia kicked in.
“There was a case in Dutch waters, near Den Helder, there was a Russian oligarch with his superyacht, and there was a lot of spoofing around the superyacht,” Pijpker said.
Jamming and Spoofing
Ayalon said that in order to carry out GPS jamming or spoofing, a bad actor needs only a relatively small high-frequency antenna, which would usually need to be sited on a tall building or on a cliff or other high place, close to a port or a shipping lane.
“They will need an antenna,” he said, adding that it is not always something that can be seen.
“It can be quite a small device,” he said.
The Norwegian shipping insurance company Gard published an article recently about GPS jamming, which said navigation in the shipping lanes of the Middle East have been impacted by GPS interference which was used as “defensive measures used to protect against drone and missile threats targeting critical infrastructure include the Israeli coast and the Red Sea during the Israel–Hamas conflict as well as the Persian Gulf and Arabian Gulf.”
Ayalon said there were a number of GPS spoofing blackspots around the world where mariners knew they had to keep especially alert.
These areas included the Black Sea, the Red Sea, the South China Sea, the Persian Gulf, the eastern end of the Mediterranean, the Barents Sea, and the seas around North Korea.
There is also a small blackspot near Pensacola, Florida, which may be linked to a U.S. naval air station.
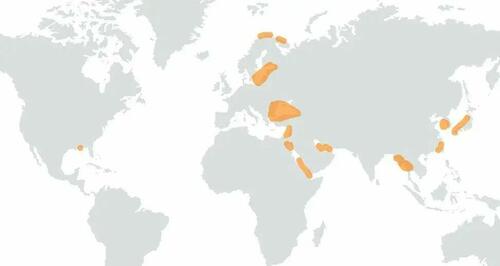 Israeli maritime cybersecurity firm Cydome’s map of GPS spoofing and jamming black spots around the world. Courtesy of Cydome
Israeli maritime cybersecurity firm Cydome’s map of GPS spoofing and jamming black spots around the world. Courtesy of CydomeAyalon said a lot of the satellite data for shipping around China was also not accurate because of spoofing.
Pijpker pointed out a case in 2019, when a British ship, the Stena Impero, drifted into Iranian waters in the Persian Gulf after apparently having its GPS spoofed.
He said the Iranians allegedly used GPS spoofing to get the ship to unintentionally enter their national waters, and they then seized it. It left Iranian waters later that year.
Ship Honeynet Created
But Pijpker said GPS spoofing remained an “under-researched topic,” and he said his own university had created a ship honeynet in an attempt to understand the “malicious traffic,” referring to a network setup with intentional vulnerabilities to attract hackers.
He said it was a “virtual ship” that was linked to the internet by a Starlink device and a decoy server and was designed “to see what kind of people are attacking ships.”
Ayalon said the increase in Low Earth Orbit (LEO) satellites like Starlink had brought with it a lot of new maritime technology, but he said a lot of crew members trust what the computer and other semi-autonomous systems display.
“This means that we see more and more events like the MSC Antonia,” he said.
He said there were a lot of tools that enabled crews to check the integrity of their GNSS, and he said crews will need to start using these types of systems “in order to make sure that they’re in the right place.”
Tyler Durden
Mon, 09/29/2025 – 17:20














